Aws Bucket Policy Stringnotlike . for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy. This element allows you to. when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. The policy i'm trying to. to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p> you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs.
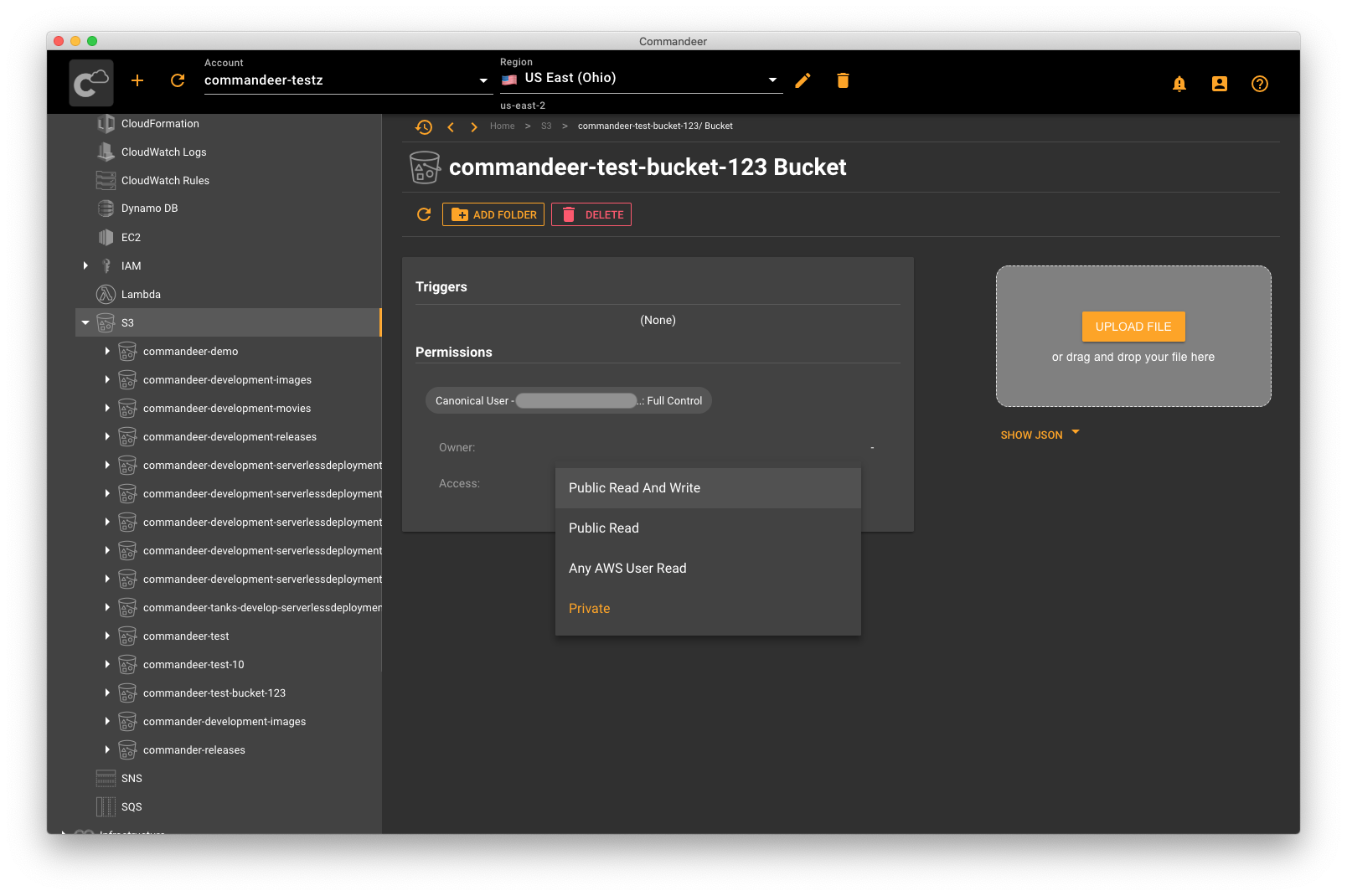
from docs.getcommandeer.com
This element allows you to. when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy. The policy i'm trying to. [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p>
Create S3 Bucket On AWS Commandeer Docs
Aws Bucket Policy Stringnotlike i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy. [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p> The policy i'm trying to. to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. This element allows you to. you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect.
From exohxdyiz.blob.core.windows.net
Terraform Resource Aws_S3_Bucket_Policy at Delores Watts blog Aws Bucket Policy Stringnotlike for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy. when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. you can use the notprincipal element of an iam or s3 bucket policy to limit. Aws Bucket Policy Stringnotlike.
From www.linkedin.com
👮AWS Security Automation Remediate Weak S3 Bucket Policies Aws Bucket Policy Stringnotlike to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a. Aws Bucket Policy Stringnotlike.
From xebia.com
Working with AWS Permission Policies Xebia Aws Bucket Policy Stringnotlike you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. This element allows you to. you can use the notprincipal element of an iam or s3 bucket. Aws Bucket Policy Stringnotlike.
From www.youtube.com
AWS 015 S3 Bucket Policy YouTube Aws Bucket Policy Stringnotlike This element allows you to. i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. you can use the optional condition element, or condition block, to specify conditions for. Aws Bucket Policy Stringnotlike.
From exokyztax.blob.core.windows.net
Aws S3 Bucket Retention Policy at Karl Olivares blog Aws Bucket Policy Stringnotlike you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. for example, the following s3 bucket policy illustrates how the previous figure is represented in a. Aws Bucket Policy Stringnotlike.
From www.armorcode.com
AWS S3 Bucket Security The Top CSPM Practices ArmorCode Aws Bucket Policy Stringnotlike i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p> to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. This element allows you to. when you. Aws Bucket Policy Stringnotlike.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Policy Stringnotlike you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. The policy i'm trying to. for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy. to prevent access to your amazon s3 buckets made by aws identity. Aws Bucket Policy Stringnotlike.
From www.techlear.com
How to create a lifecycle policy for an S3 Bucket on AWS Techlear Aws Bucket Policy Stringnotlike to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p> when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. This element allows. Aws Bucket Policy Stringnotlike.
From fig.io
aws s3control putbucketpolicy Fig Aws Bucket Policy Stringnotlike you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access. Aws Bucket Policy Stringnotlike.
From www.vrogue.co
How To Create Aws S3 Buckets With Vra Cloud 8 X Fluff vrogue.co Aws Bucket Policy Stringnotlike [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p> The policy i'm trying to. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy. . Aws Bucket Policy Stringnotlike.
From aws.amazon.com
How to Use Bucket Policies and Apply DefenseinDepth to Help Secure Aws Bucket Policy Stringnotlike i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy.. Aws Bucket Policy Stringnotlike.
From www.msp360.com
AWS IAM Policy Explained Aws Bucket Policy Stringnotlike This element allows you to. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. i am trying to write aws s3 bucket policy that denies all traffic except when it comes from two vpcs. to prevent access to your amazon s3 buckets made. Aws Bucket Policy Stringnotlike.
From www.datasciencebyexample.com
How to make AWS S3 buckets public through bucket policy DataScienceTribe Aws Bucket Policy Stringnotlike The policy i'm trying to. [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p> to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. This element allows you to. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to. Aws Bucket Policy Stringnotlike.
From www.ibm.com
Attaching an AWS S3 Bucket Aws Bucket Policy Stringnotlike when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. i am trying to write aws s3 bucket policy that denies all. Aws Bucket Policy Stringnotlike.
From dxozuwabm.blob.core.windows.net
Terraform Aws S3 Bucket Policy at David Christopher blog Aws Bucket Policy Stringnotlike when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. The policy i'm trying to. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. i am trying to. Aws Bucket Policy Stringnotlike.
From aws.amazon.com
Managing Amazon S3 access with VPC endpoints and S3 Access Points AWS Aws Bucket Policy Stringnotlike This element allows you to. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. for example, the following s3 bucket policy illustrates how the previous figure is represented in a policy. to prevent access to your amazon s3 buckets made by aws identity. Aws Bucket Policy Stringnotlike.
From www.youtube.com
AWS S3 Bucket policies indepth intuition YouTube Aws Bucket Policy Stringnotlike when you attach the managed policy to a user or a group, you grant the user or group permission to obtain a list of buckets. you can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. i am trying to write aws s3 bucket policy. Aws Bucket Policy Stringnotlike.
From docs.getcommandeer.com
Create S3 Bucket On AWS Commandeer Docs Aws Bucket Policy Stringnotlike you can use the optional condition element, or condition block, to specify conditions for when a policy is in effect. This element allows you to. to prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. [ aida:*, aida, 111111111111 ] } } } ] } can anyone.</p> when you. Aws Bucket Policy Stringnotlike.